Network Security and Vulnerability
Can you make sure for yourself how Secure Is Your Network? Do you consider it vital implementing perfect network connection?
If you manage this it will mean securing your working process since life and technologieas are ever changing and requiring persistent observation and attention.
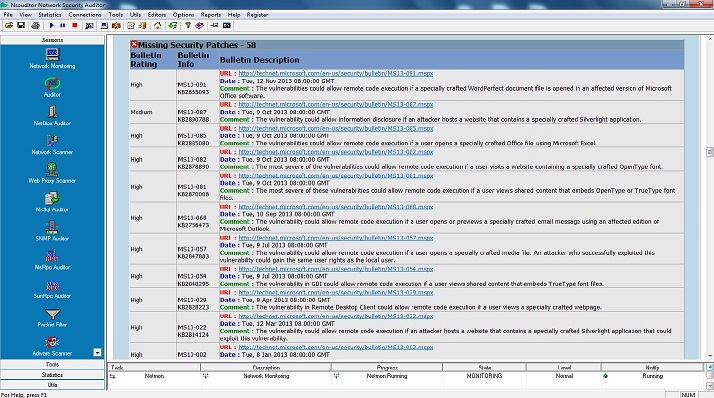
Security Vulnerabilities are among the foremost concerns for network and security professionals as it provides a critical threat for efficiency and effectiveness of an organization to meet the ever-increasing speed with which exploits are written and propagated. It is extremely important to identify network security vulnerabilities proactively before a hacker does it for planning an attack on the organization. Network security vulnerabilities are significant threat to control measures of an organization.
In computing system a vulnerability is considered a weak point giving way an intruder to shatter system’s information safety assurance.
1. The individually assigned an IDs and passwords allow access to information without additional interventionin in public, private computer networks, used in business, by governmental organizations, agencies and individuals which surely correlates and balances their activities.
For sake of all these Security Management system ( intrusion detection system) has been implemented which is called to to detect and to ‘’shelve’’ attacks.
Vulnerability management comprises the regularly repeated process of identifying, classifying, and correcting the software vulnerabilities(deficiencies) in computing systems..
In the meantime it is worh mentioning that attack can be considered active when it tries to change a system or affect its functioning. A “passive attack” aims at making use of information from the system but does not influence the system itself.
Vulnerabilities may have the following reasonable causes:
1. Complexity: Large, complex systems enhance the possibility of deficiency in a system.
2. Familiarity: Using common, widely-known code, software, operating systems, hardware enhance the possibility that an attacker can have the knowledge and tools to detect the deficiency.
3. Password management flaws: The weaker the passwords the easier to break them. The password that is stored on the computer can be accessed by a program easily since users re-use the same passwords between many programs and websites.
4. Website Browsing: Automatically installed on the computer systems harmful Spyware or Adware may become a reason for a vulnerability as the computer systems after visiting certain websites, become infected enabling others to possess the collected valuable info.
5. Software bugs: The bugs left in a software by a programmer may enable the attacker to misuse the intended tool.
So the most important circle in most information systems is the human being. He takes certain measures to physically protect the necessary personal info.
In practice, it is possible to minimize the number of intrusions by keeping systems up-to-date, using a security scanner or hiring an appropriate staff responsible for security. If you have the intention of acquiring a stable networking basis and avoid additional possibility of data loss, Nsauditor Network Security Auditor can be of great help to you appearing as an all-in-one tool for monitoring the safety of your network, providing a safe background for further activities. Nsauditor Network Security Auditor Is An Advanced All-In-One Network Tools Suite includes more than 45 network tools and utilities for network auditing, scanning, network connections monitoring and more. Nsauditor is Network Security And Vulnerability Scanner that gives you the power to scan, detect and correct any potential security risk on your network. Nsauditor allows monitoring network computers for possible vulnerabilities, checking enterprise network for all potential methods that a hacker might use to attack it and create a report of potential problems that were found. It also helps network administrators to identify security holes and deficiencies in their networked systems. A network monitor tool provides some insight into services running locally, with options to dig down into each connection and analyze the remote system, terminate connections, block unwanted network connections with incrusted firewall system and view data on the associated process.







